
Liesl Nielsen, KSL.com

Hackers penetrate voting machines used in 2016 election at SLC cybersecurity conference
By | Posted Mar 23rd, 2018 @ 6:45pm
And they’ve found a pretty major one.
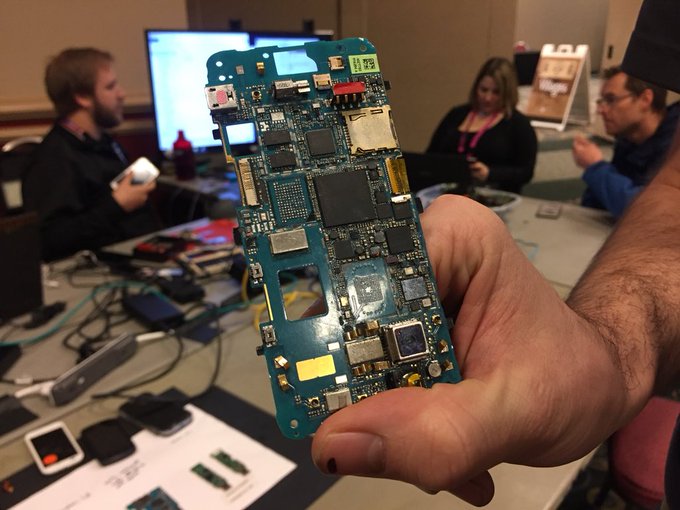
Any hacker can enter a voting booth, remove the card reader from the machine, turn off the machine, then power it back on again. Once the voting machine has turned back on, the screen will display a “no card reader” error message. All the hacker has to do from there is pop the card reader back in, and the machine will display the system setup.
With access to the system, hackers can see the network address and what is encrypting the system.
“If you know what encryption is being used, you can do what is needed to hack that encryption. You can focus your attack,” said Jake Blaney, a volunteer at HackWest.
And hackers may not even need to crack the encryption to accomplish their goal. If a voting machine is compromised, those votes are immediately suspect.
“It just creates doubt in the integrity of the system, and if that doubt is there, you could do it in a district you may not be in favor of, and those votes get thrown out,” Blaney said.
“You defend better if you know how they’re going to attack you,” he said. “We want to show what some would say are the dark arts. We show you how to break in. And then once you know how to break it, you need to know how to fix it.”
If Jackson were trying to hack, say, a journalist from KSL, he’d start by looking at her social media posts, what she shares (or overshares) and come up with a list of interests, he said.
“I can fake a common interest to gain your trust and then send you a link saying, ‘I know you like white kittens, here’s some great pictures of white kittens.’ You click the link, which goes to a site that I control that has malicious code, and I’m attacking your browser,” he said — though he mentioned that browsers will often notify users before taking them to sites that are susceptible to third-party hacks.
Most cyberattacks that target businesses exploit vulnerabilities in similar ways, but via email, Jackson noted.
This can include asking someone to visit a website or hold open a door. People will readily do something that might compromise security if they see someone in need.
“We’re good people, we’re friendly, we’re kind,” Jackson said. “If you can appear needy or you need some help, you can bend someone’s emotions to help you. And then if you can do that, you can manipulate their emotions in some other way to make them do something they wouldn’t normally do.”
Which is part of the reason Jackson hopes an understanding of cybersecurity can extend beyond the IT world. While most feel intimidated when they hear the word “cybersecurity,” taking steps to becoming more secure doesn’t have to be overly complicated, he said.
Even small steps, like coming up with good passwords or being extra vigilant with emails can pay off. It’s not just IT people that have to ensure a company’s data stays safe, Jackson said.
“Together, we’ll be more secure,” he added.
The HackWest conference will resume again next March.![]()







I remember sitting in Norma Brunson’s office in 2014 between Jim Withers and Jim Dyer watching the vote recount, and in a fit of boredom, I started chatting about the awfully poor security of modern electronic voting machines. It was fun watching Norma’s eyes widen a bit, and then narrow into angry little slits as she sputtered about how such things certainly wouldn’t be possible in Millard County’s elections (all while ignoring the box of unsecured ballots that had sat unattended in her hallway for over a week). This article brought back fun memories.